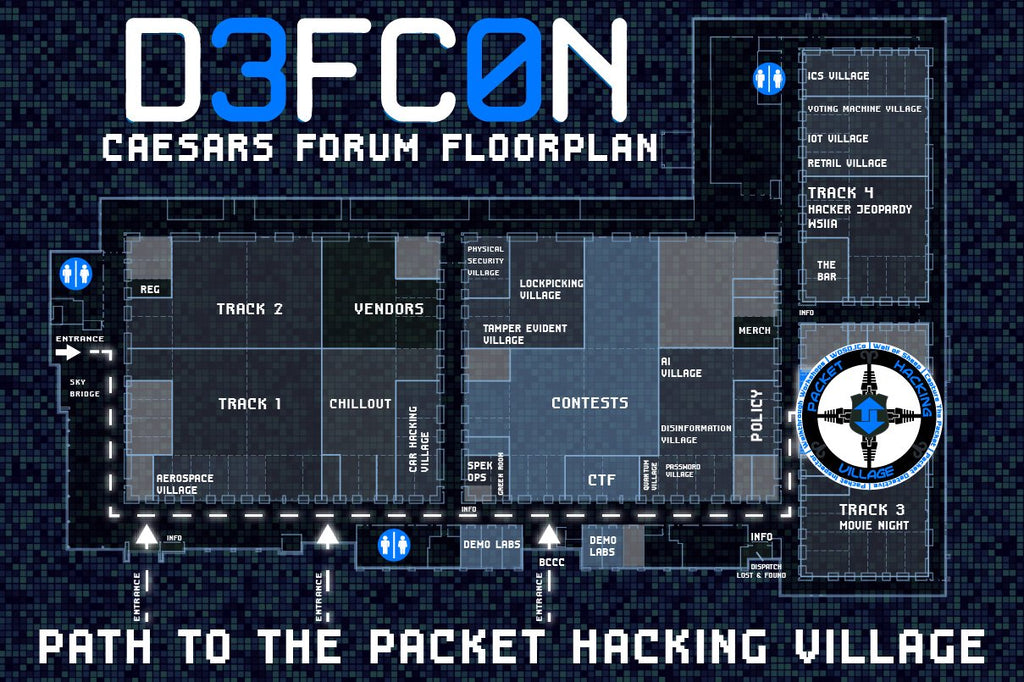
News
Accepted Packet Hacking Village / Creator Stage Talks at DEF CON 32
Date and time of each talk will be determined within next week.
Packet Hacking Village Talks at DEF CON 32 Call for Presentations Now Open
Overview
The Wall of Sheep would like to announce a call for presentations at DEF CON 32 in Las Vegas, NV from Thursday, August 8th to Sunday, August 11th. Packet Hacking Village Talks goal is to deliver talks that increase security awareness and provide skills that can be immediately applied after the conference. Our audience ranges from those who are new to security to the most seasoned practitioners in the security industry. We are accepting submissions from individuals and organizations on any of the topic areas, including, but not limited to, the following technologies and applications:
- Awareness: Security awareness program success and failure stories.
- Cloud Security: Hacks and tricks for assessing and testing services.
- Compliance: How to use regulatory compliance requirements in your favor to enhance your overall funding and security posture.
- Networking and Cybersecurity: The latest hacks, trends and technologies in networking and cybersecurity.
- Spy-level makeup art (e.g., wigs, prosthetic noses, etc.)
- Supply Chain Security: Building security into the supply chain process to reduce risk.
- Threat Defense: Advanced techniques for defending networks, systems, and services from cyberthreats.
- Tools, Techniques, and Procedures: network sniffing, intrusion detection, monitoring, forensics, DFIR log analysis, collection & visualization, threat hunting, EDR telemetry, lolbin's for defense, detecting download cradles, using the ATT&CK framework for defense, Incident response process and procedures and/or recovery, automation
DEF CON attracts a wide range of technological skill sets, presentations need to be accessible, with explanatory information to help the audience understand.
The Wall of Sheep will not accept product or vendor related pitches. If your talk is a thinly-veiled advertisement for a product or service your company is offering, please do not apply! We will also not accept talks that have been given elsewhere, including at DEF CON / Black Hat / BSides.
All accepted talks will be announced, recorded, and published by Aries Security, LLC. and DEF CON Communications, Inc. Please see our YouTube channel for all talks from previous years: https://www.youtube.com/channel/UCnL9S5Wv_dNvO381slSA06w and https://www.youtube.com/channel/UC6Om9kAkl32dWlDSNlDS9Iw.
The Call for Presentations will close on Friday, May 31st at 11:59 PM PST. The list of talks will be finalized and published on Friday, June 7th.
Speaking Format --UPDATED FOR DEF CON 32
Each presentation slot is 1 hour maximum, including time for Q&A. If we have time and it is in line with our goals mentioned above, then there is a good chance you will be selected.
Presentations will be part of DEF CON's new "Creator Stages". Although presenters will not receive a DEF CON speaker badge, they will receive a human badge and additional identification as village speakers. Presentations will also be recorded and shared on DEF CON's media servers and YouTube. Additionally, we do not recommend live demos. Pre-recorded demos are preferred.
To submit a presentation, please provide the following information in the form below to cfp2024[at]wallofsheep[dot]com
Primary Speaker Name:
Primary Speaker Title and Company (if applicable):
Primary Speaker Email Address:
Primary Speaker Phone Number (to contact you if necessary during the conference):
Primary Speaker Twitter name (if you want it known if you are accepted):
Primary Speaker Mastodon name (if you want it known if you are accepted):
Additional Speakers' name(s), titles, and social information:
Additional Email Addresses:
Is there a specific day or time you MUST speak by?
Name of Presentation:
Length of presentation: (20 minutes or 50 minutes)
Abstract (100 words MAXIMUM, absolutely necessary for printing purposes):
Your abstract will be used for the website and printed materials. Summarize what your presentation will cover. Attendees will read this to get an idea of what they should know before your presentation, and what they will learn after. Use this to inform about how technical your talk is. This abstract is the primary way people will be drawn to your session. CFP reviews like to see what tools will be used and what materials you suggest to read in advance to get the most out of your presentation.
Has this talk been given anywhere before? YES or NO
Equipment Needs & Special Requests:
The Wall of Sheep will provide 1 projector feed, and microphones. If you need to use multiple outputs for a demo, please mention this below.
Speaker's Bio(s) (75 words MAXIMUM per bio):
This text will be used for the website and printed materials and should be written in the third person. Cover any professional history that is relevant to the presentation, including past jobs, tools that you have written, etc. Let people know who you are and why you are qualified to speak on your topic. Presentations that are submitted without biographies will not be considered.
Detailed Outline:
You must provide a detailed outline containing the main points and navigation through your talk. Show how you intend to begin, where you intend to lead the audience and how you plan to get there. The outline may be provided in a separate attachment and may be as simple as a text file or as detailed as a "bare bones" presentation. The better your outline then the better we are able to best review your presentation against other submissions (and the higher chance you have of being accepted). SUBMISSION NOTE: Presentations that are submitted without abstracts, outlines, or speaker bios (e.g., that have only PDFs, PPTs, or white papers attached or only point to a URL) will not be considered.
Supporting File(s):
Additional supporting materials such as code, white papers, proof of concept, etc. should be sent along with this email to cfp2024[at]wallofsheep[dot]com. Note that additional files that may help in the selection process should be included. We are not asking for a complete presentation for this initial submission. That will only be required if you are selected for presenting.
Terms and Conditions
By submitting you agree to the Terms and Conditions below. Please read and accept these terms by inserting your name in the appropriate area, otherwise your application will be considered incomplete and returned to you.
Grant of Copyright Use
I warrant that the above work has not been previously published elsewhere, or if it has, that I have obtained permission for its publication by DEF CON Communications, Inc. and Aries Security, LLC. and that I will promptly supply DEF CON Communications, Inc. and Aries Security, LLC. with wording for crediting the original publication and copyright owner. If I am selected for presentation, I hereby give DEF CON Communications, Inc. and Aries Security, LLC. permission to duplicate, record and redistribute this presentation, which includes, but is not limited to, the conference proceedings, conference CD, video, audio, and hand-outs to the conference attendees for educational, on-line, and all other purposes.
Terms of Speaking Requirements
1. I will submit a completed (and possibly updated) presentation and a reference to all of the tool(s), law(s), Web sites and/or publications referenced to at the end of my talk and as described in this CFP submission by noon PST, July 30th, 2024. Please note this is a hard deadline as presentation and details need to be sumitted to DEF CON.
2. I will submit a final Abstract and Biography to the Wall of Sheep by noon PST, July 30th, 2024. Please note this is a hard deadline as presentation and details need to be sumitted to DEF CON.
3. I will include a detailed bibliography as either a separate document or included within the presentation of all resources cited and/or used in my presentation.
4. I will complete my presentation within the time allocated to me --not running over the time allocation.
5. I understand that I will be responsible for my own hotel and travel expenses.
Yes, I, (insert primary speaker name), have read and agree to the Grant of Copyright Use.
I, (insert your name here), have read and understand and agree to the terms as detailed in the Agreement to Terms of Speaking Requirements.
In the case that a speaker is a child under the age of 13 years old: in compliance with the Children's Online Privacy Protection Act (COPPA) regulations, http://www.coppa.org, any child under age 13 must have parental consent for the collection, use, or disclosure of that child's personal information by a website. Parent/Guardian Consent: I (insert parent/guardian's name here) am the parent or guardian of the minor/s named above. I have read and understand and agree to the terms as detailed in the Agreement to Terms of Speaking Requirements.
GoFundMe for the family of StilettoedMacgyver
There is a GoFundMe currently running to support the family of StilettoedMacgyver during this difficult time, and to help with her final expenses.
Please give as your heart directs and as you are able.
A tribute to StilettoedMacgyver
Schedule of Packet Hacking Village Talks at DEF CON 31
All talks will be held at the Village Stage in the Contest Area. You can enter via Room 232.
Friday
- 10:00: Pwning the Pwners with Mindware by Frank "D9" DiGiovanni
- 11:00: Death by 1000 Likes: How Much Do You Really Leak in Social Media? by Will Kay
- 12:00: OSINT for Physical Security Intelligence by Mike Raggo and Chet Hosmer
Saturday
- 15:00: WINE Pairing with Malware by Jared Stroud
- 16:00: The Importance of Arts and Crafts in ThreatOps by Pete Hay
Title: Pwning the Pwners with Mindware
Speaker: Frank "D9" DiGiovanni
Abstract: Traditionally the cyber attacker has an asymmetric advantage over the cyber defender. But does it have to be that way? Is it possible for the cyber defender to take an "offensive stance." This talk will show how the emerging science of cyberpsychology and the leveraging of AI can provide the defender with the ability to pwn the most vulnerable component in the cyberattack kill chain, the attack's human operator. Leveraging the DoD's "Tularosa Study," this talk will cover a theoretical framework for achieving this objective, outline an operational vignette, and then cover some the specifics for such an approach.
Speaker Bio: Forty-one years of government service, Frank DiGiovanni is a retired USAF Colonel and DoD Senior Executive Service. Co-Led with the DoD CIO the development of the SecDef's DoD Cyber Workforce Strategy. Built from scratch a six-month DoD Cyber Operations training course, repurposed DEFCON's CTF and CTP technical architecture to support DoD cyber operations training, and now working advanced cyber R&D projects in private sector. UPENN doctoral dissertation examined what makes hackers extraordinary unique from the average human population.
Title: The Importance of Arts and Crafts in ThreatOps
Speaker: Pete Hay, Editor-in-Chief, TheCyber.Report
Abstract: Cybersecurity professionals spend an huge amount of time attempting to use a visual medium to communicate complicated concepts in a simple yet information-dense manner. However if you ask 10 analysts to map out the same incident, you'll get 10 divergent diagrams. In this presentation we present a method of leveling-up your cybersecurity-related arts and crafts skills: effectively diagramming incidents, threat reports, threat intel, and reporting to support full-spectrum ThreatOps.
Speaker Bio: In addition to being SimSpace's Principal Security Strategist, Pete is the Co-Founder & Editor-in-Chief of TheCyber.Report. Pete has an extensive & diverse background in technology driven fields including Computer Network Operations (CNO), Network Forensics, & Nuclear Chemistry, as well as one of the few patents issued in Cybersecurity & ZTA. A life-long learner & security enthusiast, Pete helps Fortune 10 banks test & refine their security postures, while running TheCyber.Report as a passion project.
Title: Death by 1000 Likes: How Much Do You Really Leak in Social
Media?
Speaker: Will Kay
Abstract: As lonely Aussies attending our first Defcon last year, we were frequently drawn to the hilarity/uniquness of the Wall of Sheep board. One of our group suggested people leaking at the con was super entertaining, but what about throughout the rest of the year? We decided to use the time between DC30 and DC31 scraping the r/defcon subreddit to create the Wall of Sheep - online edition.
Speaker Bio: Will works for a private security consultancy in Australia. He is cybersecurity advisor and insider threat consultant. His professional career began many years ago in military intelligence to which he owes his knowledge of traditional targeting methods. The organisation and team he works for today provides security awareness and reinforcement training. His passion is removing the weakness that exists across society to social engineering techniques, and believes a more secure and prosperous future begins with people.
Title: OSINT for Physical Security Intelligence
Speakers: Mike Raggo, Security Researcher, SilentSignals; Chet Hosmer,
Chief Scientist
Abstract: Organizations seek rapid intelligence about critical situations that impact their teams, locations, or assets. Yet when it comes to OSINT we find organizations performing Open Source Information gathering; wasting time sifting through data to get to the actionable intelligence. In this presentation we demonstrate how to collect curated data and eliminate 99% of the time spent on reliminary data analysis. Furthermore, all of this data can be combined to perform trending and predictive analysis for natural disasters, geo-political situations, or business risk. The goal is to provide attendees with ideas for formulating new approaches for physical security OSINT.
Speaker Bios: Michael T. Raggo has over 30 years of security research experience. During this time, he has uncovered and ethically disclosed vulnerabilities in products including Samsung, Checkpoint, and Netgear. Michael is the author of "Mobile Data Loss: Threats &Countermeasures" and "Data Hiding" for Syngress Book. He is also a frequent presenter at security conferences, including Black Hat, DEF CON, Gartner, RSA, DoD Cyber Crime, OWASP, SANS. He was also awarded the Pentagon's Certificate of Appreciation.
Chet Hosmer is an international author, educator, researcher, and founder of Python Forensics, Inc., a non-profit research institute focused on the collaborative development of open source investigative technologies using the Python programming language. Chet is also a Visiting Professor at Utica College in the Cybersecurity Graduate Program, where his research and teaching is focused on data hiding, active cyber defense and security of industrial control systems. Additionally, Chet is an Adjunct Professor at Champlain College in the Digital Forensics Graduate Program, where his research and teaching is focused on solving hard digital investigation problems using the Python programming language.
Title: WINE Pairing with Malware
Speaker: Jared Stroud, Lead Security Engineer, The MITRE Corporation
Abstract: The growing popularity of playing AAA Windows video games on Linux has increased the compatibility of tools such as WINE and Proton. These same platforms that enable the latest games to run also can be used to execute the latest Malware. This talk will walk through configuring an environment to rapidly collect IoCs from unknown samples without having to use expensive sandboxes. Learn how to leverage your favorite UNIX tools to awk, grep, and pipe your way to extracting valuable forensic evidence without submitting your samples to $VENDOR. More on the offensive side? Come see how to shorten the feedback loop from idea generation, to testing and finally deployment!
Speaker Bio: Jared Stroud is a Lead Security Engineer at The MITRE Corporation tackling problems related to Container and Kubernetes security. Jared also contributes to ATT&CK via Adversary Emulation for Linux threats.
Packet Hacking Village Talks at DEF CON 31
Talks at DEF CON 31. Times and location of talks will be announced
soon.
**********
Title: Pwning the Pwners with Mindware
Speaker: Frank "D9" DiGiovanni
Abstract: Traditionally the cyber attacker has an asymmetric advantage
over the cyber defender. But does it have to be that way? Is it
possible for the cyber defender to take an "offensive stance." This
talk will show how the emerging science of cyberpsychology and the
leveraging of AI can provide the defender with the ability to pwn the
most vulnerable component in the cyberattack kill chain, the attack's
human operator. Leveraging the DoD's "Tularosa Study," this talk will
cover a theoretical framework for achieving this objective, outline an
operational vignette, and then cover some the specifics for such an
approach.
Speaker Bio: Forty-one years of government service, Frank DiGiovanni
is a retired USAF Colonel and DoD Senior Executive Service. Co-Led
with the DoD CIO the development of the SecDef's DoD Cyber Workforce
Strategy. Built from scratch a six-month DoD Cyber Operations training
course, repurposed DEFCON's CTF and CTP technical architecture to
support DoD cyber operations training, and now working advanced cyber
R&D projects in private sector. UPENN doctoral dissertation examined
what makes hackers extraordinary unique from the average human
population.
**********
Title: The Importance of Arts and Crafts in ThreatOps
Speaker: Pete Hay, Editor-in-Chief, TheCyber.Report
Abstract: Cybersecurity professionals spend an huge amount of time
attempting to use a visual medium to communicate complicated concepts
in a simple yet information-dense manner. However if you ask 10
analysts to map out the same incident, you'll get 10 divergent
diagrams. In this presentation we present a method of leveling-up your
cybersecurity-related arts and crafts skills: effectively diagramming
incidents, threat reports, threat intel, and reporting to support
full-spectrum ThreatOps.
Speaker Bio: In addition to being SimSpace's Principal Security
Strategist, Pete is the Co-Founder & Editor-in-Chief of
TheCyber.Report. Pete has an extensive & diverse background in
technology driven fields including Computer Network Operations (CNO),
Network Forensics, & Nuclear Chemistry, as well as one of the few
patents issued in Cybersecurity & ZTA. A life-long learner & security
enthusiast, Pete helps Fortune 10 banks test & refine their security
postures, while running TheCyber.Report as a passion project.
**********
Title: Death by 1000 Likes: How Much Do You Really Leak in Social
Media?
Speaker: Will Kay
Abstract: As lonely Aussies attending our first Defcon last year, we
were frequently drawn to the hilarity/uniquness of the Wall of Sheep
board. One of our group suggested people leaking at the con was super
entertaining, but what about throughout the rest of the year? We
decided to use the time between DC30 and DC31 scraping the r/defcon
subreddit to create the Wall of Sheep - online edition.
Speaker Bio: Will works for a private security consultancy in
Australia. He is cybersecurity advisor and insider threat
consultant. His professional career began many years ago in military
intelligence to which he owes his knowledge of traditional targeting
methods. The organisation and team he works for today provides
security awareness and reinforcement training. His passion is removing
the weakness that exists across society to social engineering
techniques, and believes a more secure and prosperous future begins
with people.
**********
Title: OSINT for Physical Security Intelligence
Speakers: Mike Raggo, Security Researcher, SilentSignals; Chet Hosmer,
Chief Scientist
Abstract: Organizations seek rapid intelligence about critical
situations that impact their teams, locations, or assets. Yet when it
comes to OSINT we find organizations performing Open Source
Information gathering; wasting time sifting through data to get to the
actionable intelligence. In this presentation we demonstrate how to
collect curated data and eliminate 99% of the time spent on
preliminary data analysis. Furthermore, all of this data can be
combined to perform trending and predictive analysis for natural
disasters, geo-political situations, or business risk. The goal is to
provide attendees with ideas for formulating new approaches for
physical security OSINT.
Speaker Bios: Michael T. Raggo has over 30 years of security research
experience. During this time, he has uncovered and ethically disclosed
vulnerabilities in products including Samsung, Checkpoint, and
Netgear. Michael is the author of "Mobile Data Loss: Threats &
Countermeasures" and "Data Hiding" for Syngress Book. He is also a
frequent presenter at security conferences, including Black Hat, DEF
CON, Gartner, RSA, DoD Cyber Crime, OWASP, SANS. He was also awarded
the Pentagon's Certificate of Appreciation.
Chet Hosmer is an international author, educator, researcher, and
founder of Python Forensics, Inc., a non-profit research institute
focused on the collaborative development of open source investigative
technologies using the Python programming language. Chet is also a
Visiting Professor at Utica College in the Cybersecurity Graduate
Program, where his research and teaching is focused on data hiding,
active cyber defense and security of industrial control
systems. Additionally, Chet is an Adjunct Professor at Champlain
College in the Digital Forensics Graduate Program, where his research
and teaching is focused on solving hard digital investigation problems
using the Python programming language.
**********
Title: WINE Pairing with Malware
Speaker: Jared Stroud, Lead Security Engineer, The MITRE Corporation
Abstract: The growing popularity of playing AAA Windows video games on
Linux has increased the compatibility of tools such as WINE and
Proton. These same platforms that enable the latest games to run also
can be used to execute the latest Malware. This talk will walk
through configuring an environment to rapidly collect IoCs from
unknown samples without having to use expensive sandboxes. Learn how
to leverage your favorite UNIX tools to awk, grep, and pipe your way
to extracting valuable forensic evidence without submitting your
samples to $VENDOR. More on the offensive side? Come see how to
shorten the feedback loop from idea generation, to testing and finally
deployment!
Speaker Bio: Jared Stroud is a Lead Security Engineer at The MITRE
Corporation tackling problems related to Container and Kubernetes
security. Jared also contributes to ATT&CK via Adversary Emulation
for Linux threats.
Packet Hacking Village Talks at DEF CON 31 Call for Presentations Now Open
Overview
The Wall of Sheep would like to announce a call for presentations at DEF CON 31 in Las Vegas, NV from Thursday, August 10th to Sunday, August 13th. Packet Hacking Village Talks goal is to deliver talks that increase security awareness and provide skills that can be immediately applied after the conference. Our audience ranges from those who are new to security to the most seasoned practitioners in the security industry. We are accepting submissions from individuals and organizations on any of the topic areas, including, but not limited to, the following technologies and applications:
- Awareness: Security awareness program success and failure stories.
- Cloud Security: Hacks and tricks for assessing and testing services.
- Compliance: How to use regulatory compliance requirements in your favor to enhance your overall funding and security posture.
- Networking and Cybersecurity: The latest hacks, trends and technologies in networking and cybersecurity.
- Spy-level makeup art (e.g., wigs, prosthetic noses, etc.)
- Supply Chain Security: Building security into the supply chain process to reduce risk.
- Threat Defense: Advanced techniques for defending networks, systems, and services from cyberthreats.
- Tools, Techniques, and Procedures: network sniffing, intrusion detection, monitoring, forensics, DFIR log analysis, collection & visualization, threat hunting, EDR telemetry, lolbin's for defense, detecting download cradles, using the ATT&CK framework for defense, Incident response process and procedures and/or recovery, automation
DEF CON attracts a wide range of technological skill sets, presentations need to be accessible, with explanatory information to help the audience understand.
The Wall of Sheep will not accept product or vendor related pitches. If your talk is a thinly-veiled advertisement for a product or service your company is offering, please do not apply! We will also not accept talks that have been given elsewhere, including at DEF CON / Black Hat / BSides.
All accepted talks will be announced, recorded, and published by Aries Security, LLC. and DEF CON Communications, Inc. Please see our YouTube channel for all talks from previous years: https://www.youtube.com/channel/UCnL9S5Wv_dNvO381slSA06w and https://www.youtube.com/channel/UC6Om9kAkl32dWlDSNlDS9Iw.
The Call for Presentations will close on Friday, June 16th at 11:59 PM PST. The list of talks will be finalized and published on Friday, June 30th.
Speaking Format --UPDATED FOR DEF CON 31
Each presentation slot is 1 hour maximum, including time for Q&A. If we have time and it is in line with our goals mentioned above, then there is a good chance you will be selected.
Presentations will be hosted from the Packet Hacking Village where they will be simulcast live over Discord Stages. This is a compromise to save space and maximize participation and engagement. Q+A will be available digitally and speakers should be prepared to answer questions that come in online.
To submit a presentation, please provide the following information in the form below to cfp2023[at]wallofsheep[dot]com
Primary Speaker Name:
Primary Speaker Title and Company (if applicable):
Primary Speaker Email Address:
Primary Speaker Phone Number (to contact you if necessary during the conference):
Primary Speaker Twitter name (if you want it known if you are accepted):
Primary Speaker Mastodon name (if you want it known if you are accepted):
Additional Speakers' name(s), titles, and social information:
Additional Email Addresses:
Is there a specific day or time you MUST speak by?
Name of Presentation:
Length of presentation: (20 minutes or 50 minutes)
Abstract (100 words MAXIMUM, absolutely necessary for printing purposes):
Your abstract will be used for the website and printed materials. Summarize what your presentation will cover. Attendees will read this to get an idea of what they should know before your presentation, and what they will learn after. Use this to inform about how technical your talk is. This abstract is the primary way people will be drawn to your session. CFP reviews like to see what tools will be used and what materials you suggest to read in advance to get the most out of your presentation.
Has this talk been given anywhere before? YES or NO
Equipment Needs & Special Requests:
The Wall of Sheep will provide 1 projector feed, and microphones. If you need to use multiple outputs for a demo, please mention this below.
Speaker's Bio(s) (75 words MAXIMUM per bio):
This text will be used for the website and printed materials and should be written in the third person. Cover any professional history that is relevant to the presentation, including past jobs, tools that you have written, etc. Let people know who you are and why you are qualified to speak on your topic. Presentations that are submitted without biographies will not be considered.
Detailed Outline:
You must provide a detailed outline containing the main points and navigation through your talk. Show how you intend to begin, where you intend to lead the audience and how you plan to get there. The outline may be provided in a separate attachment and may be as simple as a text file or as detailed as a "bare bones" presentation. The better your outline then the better we are able to best review your presentation against other submissions (and the higher chance you have of being accepted). SUBMISSION NOTE: Presentations that are submitted without abstracts, outlines, or speaker bios (e.g., that have only PDFs, PPTs, or white papers attached or only point to a URL) will not be considered.
Supporting File(s):
Additional supporting materials such as code, white papers, proof of concept, etc. should be sent along with this email to cfp2023[at]wallofsheep[dot]com. Note that additional files that may help in the selection process should be included. We are not asking for a complete presentation for this initial submission. That will only be required if you are selected for presenting.
Terms and Conditions
By submitting you agree to the Terms and Conditions below. Please read and accept these terms by inserting your name in the appropriate area, otherwise your application will be considered incomplete and returned to you.
Grant of Copyright Use
I warrant that the above work has not been previously published elsewhere, or if it has, that I have obtained permission for its publication by DEF CON Communications, Inc. and Aries Security, LLC. and that I will promptly supply DEF CON Communications, Inc. and Aries Security, LLC. with wording for crediting the original publication and copyright owner. If I am selected for presentation, I hereby give DEF CON Communications, Inc. and Aries Security, LLC. permission to duplicate, record and redistribute this presentation, which includes, but is not limited to, the conference proceedings, conference CD, video, audio, and hand-outs to the conference attendees for educational, on-line, and all other purposes.
Terms of Speaking Requirements
1. I will submit a completed (and possibly updated) presentation and a reference to all of the tool(s), law(s), Web sites and/or publications referenced to at the end of my talk and as described in this CFP submission by noon PST, June 30th, 2023.
2. I will submit a final Abstract and Biography to the Wall of Sheep by noon PST, June 30th, 2023.
3. I will include a detailed bibliography as either a separate document or included within the presentation of all resources cited and/or used in my presentation.
4. I will complete my presentation within the time allocated to me --not running over the time allocation.
5. I understand that the Wall of Sheep will provide 1 LCD projector feed, 2 screens, and microphones. I understand that I am responsible for providing all other necessary equipment, including laptops and machines (with VGA output), to complete my presentation.
6. I understand that I will be responsible for my own hotel and travel expenses, and admissions to the DEF CON Conference.
Yes, I, (insert primary speaker name), have read and agree to the Grant of Copyright Use.
I, (insert your name here), have read and understand and agree to the terms as detailed in the Agreement to Terms of Speaking Requirements.
In the case that a speaker is a child under the age of 13 years old: in compliance with the Children's Online Privacy Protection Act (COPPA) regulations, http://www.coppa.org, any child under age 13 must have parental consent for the collection, use, or disclosure of that child's personal information by a website. Parent/Guardian Consent: I (insert parent/guardian's name here) am the parent or guardian of the minor/s named above. I have read and understand and agree to the terms as detailed in the Agreement to Terms of Speaking Requirements.
WoSDJCO at DEF CON 30 Schedule
| Thursday, August 11th | Friday, August 12th | Saturday, August 13th | Sunday, August 14th | |
|---|---|---|---|---|
| 10:00 |
PHV will be doing load/unload and setup all day. Feel free to come around and say hello. If we have gear, there will be beats. |
Funktribe | Canyon | kampf |
| 11:00 | phreakocious | Y&T | kampf | |
| 12:00 | tense x phreak | Deep Therapy | Athlex | |
| 13:00 | Tense Future | Miss Jackalope | Closing Ceremony | |
| 14:00 | Y&T | icetre normal | ||
| 15:00 | Hanz Dwight | phreakocious | ||
| 16:00 | DotOrNot | tavoo | ||
| 17:00 | heckseven + pals | T A N |
DJ Bios
phreakocious (@phreakocious, https://mixcloud.com/phreakocious)
I press enter!
tense future (@tensefutur3, https://www.mixcloud.com/tensefuture/)
sync & destroy
Yesterday & Tomorrow (Y&T) (https://takeyouto.space)
I'd like to buy a vowel.
Athlex (@brokenjetpack, https://www.mixcloud.com/athlex/)
oontz oontz oontz
Canyon (@canyon289, file:///dev/null)
"Published a book and stuff. math is cool" is what someone thinks I would write in my bio.
Deep Therapy (@therapy_life, https://www.mixcloud.com/SoundboxMiami)
oontz oontz oontz
DotOrNot (@dotornot2, https://www.mixcloud.com/dotornot/)
Are you the police? No Ma'am, we're DJs
Funktribe
Hanz Dwight (https://linktr.ee/hanzdwight)
One time in 2018, he got a noise complaint for playing music in the middle of the Mojave desert.
heckseven, eg0n, bbartokk, Iggs Boson (https://heckseven.com, https://bbartokk.com)
synth freaks, massive beats, plywood boxes, spicy grooves
Icetre Normal (@IcetreNormal, https://www.youtube.com/channel/UCVY8zEm23QFbO-7LfWLR6xg)
"When I eat fire, you shouldn't think about how I'm doing it; I really do get burned. You should think about -why-..." -Penn Jillette
kampf (@nerd_show, https://www.mixcloud.com/NerdShow)
With over a decade of experience as a college radio DJ at KWCR on Nerd Show, kampf has waded long and deep through the muddied waters of electronic music, casting his rod time and again to obtain, then share the eclectic, the compelling, the sounds off the beaten path and those lesser know varieties or species. Resident DJ for the DEF CON Chillout Lounge and for DEF CON Radio on SomaFM.com. Spinning vinyl for WoS/Packet Hacking Village since DEF CON 20!
Miss Jackalope (@djjackalope, https://www.mixcloud.com/djjackalope/)
Miss Jackalope is DEF CON's resident community DJ. She has a weekly Twitch show and a legendary Jackalope Army merch store. She plays drum and bass and bass house and is known for ceiling destruction! Happy to be back at the PHV!
tavoo (https://tavoo.co, https://soundcloud.com/tavootech)
Devoted disciple of the darker electronic sounds. Specializing in murky shades of Techno, D&B, and everything in-between.
Terrestrial Access Network (T A N)
crunchy kicks and bleeps and bloops from outer space
Capture The Packet Competition Details at DEF CON 30


Packet Hacking Village at DEF CON 30
The Packet Hacking Village at DEF CON 30 will be in-person only. Our village hours:
- Friday, August 12th: 10:00 - 18:00
- Saturday, August 13th: 10:00 - 18:00
- Sunday, August 14th: 10:00 - 13:00
All times are in PDT. Schedules are subject to change.

Events and Contests
- Packet Inspector
- Packet Detective
- Capture The Packet
-
Walkthrough Workshops (WTW)
- Hardwired (NEW for 2022)
- Honeypots
- Linux Trainer (NEW for 2022)
- NetworkOS: Be The Cloud (NEW for 2022)
- Regular Expressions (RegEx) Trainer (NEW for 2022)
- WoSDJCO
Packet Inspector
The perfect introduction to network analysis, sniffing, and forensics. Do you want to understand the techniques people use to tap into a network, steal passwords and listen to conversations? Packet Inspector is the place to develop these skills! For well over a decade, the Wall of Sheep has shown people how important it is to use end-to-end encryption to keep sensitive information like passwords private. Using a license of the world famous Capture The Packet engine from Aries Security, we have created a unique way to teach hands-on skills in a controlled real-time environment.
Packet Detective
Looking to upgrade your skills or see how you would fare in Capture The Packet? Come check out what Packet Detective has to offer! A step up in difficulty from Packet Inspector, Packet Detective will put your network hunting abilities to the test with real-world scenarios at the intermediate level. Take the next step in your journey towards network mastery in a friendly environment still focused on learning and take another step closer to preparing yourself for the competitive environment of Capture The Packet.
Capture The Packet
Come compete in the world's most challenging cyber defense competition based on the Aries Security Cyber Range. Tear through the challenges, traverse a hostile enterprise class network, and diligently analyze what is found in order to make it out unscathed. Not only glory, but prizes await those that emerge victorious from this upgraded labyrinth, so only the best prepared and battle hardened will escape the crucible.


Walkthrough Workshops (WTW)
Hardwired
Don't know how to make a network cable and want to learn? Has it been years? Or do you think you're a pro? Come see if you can... make the best cable at con by cut/wire/crimp.
Honeypots
You are the world's greatest hacker. You find vulnerable machine open to SSH and brute force the root credentials easily! Hooray! But wait, are you actually on a vulnerable machine full of secrets, or a honeypot logging your every keystroke?
In this half hour workshop, you'll get your very own Cowrie honeypot (https://github.com/cowrie/cowrie) running on Ubuntu, and learn how to modify it, administer it, and watch the logs for hackers in action!
This workshop is great for both advanced Linux users who want to learn a new skill or those who have never used Linux before! We'll give you command-by-command instructions along with helpful guidance and starting points if you want to go off and do something cool.
Linux Trainer
Knowing how to use the Linux command line is a critical skill for any good security practitioner. This trainer will have 10+ problems covering some of the most fundamental Linux commands. This trainer is for people new to field and for those who want to hone their Linux command line-fu.
NetworkOS: Be The Cloud
The NetworkOS workshop will take you into the mysterious world which underpins modern computing and allows people to talk across the globe. This of course being the network itself. In this workshop you will familiarize yourself with the command line of network devices. Step by step, you will configure devices to talk to each other, share information about the computers connected to them, and relay their network information and traffic between each other. No experience needed, know how to type and copy/paste.
Regular Expressions (RegEx) Trainer
Regular Expressions or RegEX are used everywhere! If you aspire to be a Pentester, Threat Hunter, Programmer, Network Engineer, DevOps or really anything in technology today, RegEx is a skill all the greats have and the majority of the industry are terrible at. Come learn or brush up on your RegEx skills in on our live trainer.
WoSDJCO
| Thursday, August 11th | Friday, August 12th | Saturday, August 13th | Sunday, August 14th | |
|---|---|---|---|---|
| 10:00 |
PHV will be doing load/unload and setup all day. Feel free to come around and say hello. If we have gear, there will be beats. |
Funktribe | Canyon | kampf |
| 11:00 | phreakocious | Y&T | kampf | |
| 12:00 | tense x phreak | Deep Therapy | Athlex | |
| 13:00 | Tense Future | Miss Jackalope | Closing Ceremony | |
| 14:00 | Y&T | icetre normal | ||
| 15:00 | Hanz Dwight | phreakocious | ||
| 16:00 | DotOrNot | tavoo | ||
| 17:00 | heckseven + pals | T A N |
DJ Bios
phreakocious (@phreakocious, https://mixcloud.com/phreakocious)
I press enter!
tense future (@tensefutur3, https://www.mixcloud.com/tensefuture/)
sync & destroy
Yesterday & Tomorrow (Y&T) (https://takeyouto.space)
I'd like to buy a vowel.
Athlex (@brokenjetpack, https://www.mixcloud.com/athlex/)
oontz oontz oontz
Canyon (@canyon289, file:///dev/null)
"Published a book and stuff. math is cool" is what someone thinks I would write in my bio.
Deep Therapy (@therapy_life, https://www.mixcloud.com/SoundboxMiami)
oontz oontz oontz
DotOrNot (@dotornot2, https://www.mixcloud.com/dotornot/)
Are you the police? No Ma'am, we're DJs
Funktribe
Hanz Dwight (https://linktr.ee/hanzdwight)
One time in 2018, he got a noise complaint for playing music in the middle of the Mojave desert.
heckseven, eg0n, bbartokk, Iggs Boson (https://heckseven.com, https://bbartokk.com)
synth freaks, massive beats, plywood boxes, spicy grooves
Icetre Normal (@IcetreNormal, https://www.youtube.com/channel/UCVY8zEm23QFbO-7LfWLR6xg)
"When I eat fire, you shouldn't think about how I'm doing it; I really do get burned. You should think about -why-..." -Penn Jillette
kampf (@nerd_show, https://www.mixcloud.com/NerdShow)
With over a decade of experience as a college radio DJ at KWCR on Nerd Show, kampf has waded long and deep through the muddied waters of electronic music, casting his rod time and again to obtain, then share the eclectic, the compelling, the sounds off the beaten path and those lesser know varieties or species. Resident DJ for the DEF CON Chillout Lounge and for DEF CON Radio on SomaFM.com. Spinning vinyl for WoS/Packet Hacking Village since DEF CON 20!
Miss Jackalope (@djjackalope, https://www.mixcloud.com/djjackalope/)
Miss Jackalope is DEF CON's resident community DJ. She has a weekly Twitch show and a legendary Jackalope Army merch store. She plays drum and bass and bass house and is known for ceiling destruction! Happy to be back at the PHV!
tavoo (https://tavoo.co, https://soundcloud.com/tavootech)
Devoted disciple of the darker electronic sounds. Specializing in murky shades of Techno, D&B, and everything in-between.
Terrestrial Access Network (T A N)
crunchy kicks and bleeps and bloops from outer space